I’m in San Diego presenting at the Shareholders Service Group 2013 conference, then headed out to Palm Springs tomorrow for FPA Retreat 2013. Grab me and introduce yourself if you’re attending either event!
Here are this weeks stories of interest:
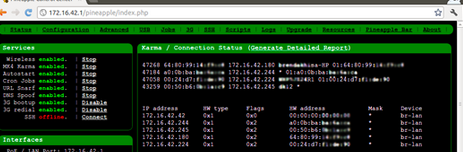
How to secure mobile devices against “WiFi honeypots” from FPPad
[This is important, so I’m sharing it in the first spot this week. WiFi honeypots are hardware devices that fool your laptop and/or mobile device into thinking its connected to a trusted WiFi network. But its not, and unknowingly connecting to a WiFi honeypot exposes you to a man-in-the-middle attack. Read this article now to learn how you can increase your defenses against WiFi honeypots.] Most of the time, you’re likely not at risk of having data you send over WiFi intercepted by someone else. But a number of software programs and hardware devices for sale on the Internet allow users to do just that; sit on public WiFi and eavesdrop on unencrypted data being passed back and forth.
Pershing Broadens the Accessibility of NetX360 to run on Microsoft’s Surface Pro Tablet from PRNewswire
[Ok, the race to support Windows 8 is on. Pershing starts off the PR campaign by announcing its NetX360 custodial platform is now supported on Windows 8. By definition, that means NetX360 also runs on Surface Pro tablets, which run Windows 8. BUT, what I haven’t seen yet is the user interface, and I doubt there have been any major changes to the interface that correspond with the tiles UI (formerly Metro) featured so prominently in Windows 8. I’d reach out to Pershing for comment, but I’m 35,000 feet in the air as I write this.] Pershing LLC, a BNY Mellon company, today announced that the company’s industry-leading technology platform for advisors, NetX360®, now runs on Microsoft’s new Surface™ Pro tablet. The availability and compatibility of NetX360 on the Surface Pro will help advisors manage their business more effectively and efficiently while working in the office or on the road.
Building a Smarter Portfolio from Financial-Planning.com
[Joel Bruckenstein reviews Riskalyze, a web-based tool that uses questionnaires to determine a quantifiable number for a client’s risk tolerance. With the “magic” number in hand, advisers can design portfolios around the client’s appetite (or lack thereof) for risk. Sound familiar? As Bruckenstein mentioned, providers like MoneyGuidePro and FinaMetrica have similar features in their respective programs. But the fresh graphics and appealing user interface give Riskalyze a leg up on the usability factor, so this is one worth watching as they mature.] I recently tried a new cloud-based product called Riskalyze Pro that provides advisors with both risk-assessment and portfolio-construction tools. The tool was developed by Riskalyze Advisors, a new company whose proprietary platform provides risk assessment, portfolio construction, analytics and investment discovery.
eMoney And Zumbox Announce Strategic Partnership To Offer Digital Postal Mail To Clients from PRNewswire
[Here’s an interesting combination. Zumbox is an alternative to paper mail you get every day. Instead, Zumbox scans all your paper mail and delivers it to you through a secure portal. That worked well five years ago when everything came in the mail. I don’t know about you, but today, I get virtually everything electronically, including bank statements, credit card statements, brokerage account trade confirms. Even my tax return this year was 100% electronic. So why eMoney chooses to partner with Zumbox for electronic document delivery over more prevalent providers (say, ShareFile, Box, etc.)? I’m going to connect with eMoney soon, so I’ll report back what I learn.] eMoney Advisor (“eMoney”), the only wealth-planning system for financial advisors that offers transparency, security, mobile access and superior organization for everything that impacts their clients’ financial lives, has announced a strategic partnership with Zumbox to offer Digital Postal Mail to clients whose advisors use the eMoney platform.