
A security flaw dubbed “Heartbleed” has the potential to affect financial advisers and their clients
This is an evolving story, so in the interest in providing financial advisers with pertinent information about a serious vulnerability in Internet security, I’m offering this guide in a FAQ format.
What is Heartbleed?
Basically, “Heartbleed” is the name of a bug in software that many web-based services use to secure connections over the internet called OpenSSL. When you see the green padlock icon in your web browser’s address bar, chances are your online Internet session is encrypted with some form of the OpenSSL protocol.
The Heartbleed bug, discovered earlier this week, allows an attacker to use messages called “heartbeats” to trick a server into passing along sensitive information from its memory. The information could include account passwords or the server’s private encryption keys.
When hackers get access to that information, really bad things can happen.
Lots of additional details on Heartbleed can be found online, but you can start with the Wikipedia entry that is being updated in real time: http://en.wikipedia.org/wiki/Heartbleed
How do I test a site if it’s vulnerable to Heartbleed?
Go to this website and type in the domain name of the service you want to test: http://filippo.io/Heartbleed/
The site I tested is vulnerable to Heartbleed! What do I do now?
Oh no! First, assume that your password has been compromised. If you use the same password for other online services, identify the other sites where it’s used.
BUT WAIT! Don’t reset your passwords on the vulnerable sites just yet!
You need to wait until the vendor updates their OpenSSL code to eliminate the vulnerability. Only AFTER you receive confirmation from the vendor that OpenSSL has been updated will it be safe to return to the service and reset your password. Next, skip to the question on multi-factor authentication to increase the security of your online accounts.
The site I tested is all clear. What do I do now?
Whew, what a relief! That one site hasn’t been exposed, but your passwords still may have been exposed from another site. One thing you can easily do to enhance the security of your account is to activate multi-factor authentication (see below).
What’s the multi-factor authentication you mentioned?
Multi-factor authentication is a process where you use two or more factors to successfully log in to a secure account. The “factors” take three forms:
- Something You Know, like your username, password, PIN, or finger gesture pattern.
- Something You Have, like your ATM card, security token, smartcard, or mobile phone.
- Something You Are, like your fingerprint, retina, voice, or typing rhythm.
Combining two or more of these factors substantially increases the difficulty of compromising your online account.
Assume that your password was compromised due to the Heartbleed bug and a hacker attempts to use it. If you implemented multi-factor authentication, the hacker also needs to satisfy the second factor of authentication in order to access your account. If you use your mobile phone to receive a login code, the hacker would not only need to know your password but also have physical access to your mobile phone to identify the login code.
Is there list that shows what sites support multi-factor authentication?
I’m glad you asked! Last week I identified an outstanding resource on multi-factor authentication in this post, Who supports two factor authentication? Find out in this awesome chart.
The site is twofactorauth.org and it’s totally worth your time right now to review the list of services and activate multi-factor authentication for any login
Can I do something to my web browser to validate the security of my session?
Yes, you can tweak your web browser settings to enforce more stringent security settings for your online sessions. While it’s not a guarantee against the Heartbleed vulnerability, the settings shown below will check if a site’s security certificate has been revoked before establishing a connection.
With thanks to Levi on Twitter, here are some changes you can make to Chrome and Firefox:
@jrconlin @_jden For Firefox users (all 9 of us): Options -> Advanced -> Certificates -> Validation -> “When OSPC fails, treat as invalid”
— Levi (@not_levi) April 9, 2014
Also, courtesy of Dan Santner, here is a link to a more comprehensive scanning tool for a server’s SSL integrity:
@BillWinterberg if your readers want a more comprehensive overall SSL test https://t.co/mgvJ38zGwL
— Dan Santner (@dansantner) April 10, 2014
The results of that test resemble a grade shown below:
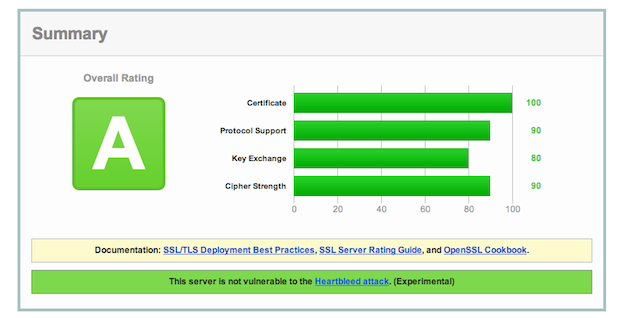
A report generated by the Qualys SSL Server Test
Add your questions below
Did I miss any important details? Is something unclear in one of my answers?
Let me know in the comments below and I’ll update this FAQ accordingly.




