On today’s broadcast, a serious security flaw impacts two-thirds of the Internet. How this may affect the information you store online. Betterment announces the launch of an Institutional platform. Will they start winning turnkey asset management business from advisors? And learn how a new integration between Redtail and Riskalyze will help you monitor client portfolios to keep them in line with your client’s risk tolerance.
So get ready, FPPad Bits and Bytes begins now!
(Watch FPPad Bits and Bytes on YouTube)
Today’s episode is brought to you by Wealthbox CRM. Wealthbox is collaborative, social, and outrageously simple CRM for financial advisors.
Sign up for a free trial today by visiting fppad.com/wealthbox
Here are the links to this week’s top stories:
Here’s everything you need to know about the Heartbleed web security flaw from Gigaom, and
The Heartbleed FAQ for financial advisers from FPPad
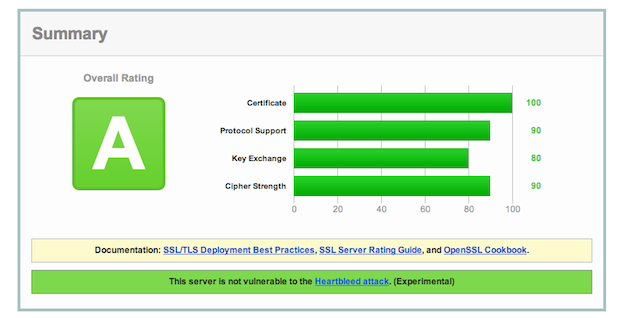
[Leading off this week’s broadcast is news of a critical security flaw in a web browser encryption standard called OpenSSL, in use by an estimated two-thirds of all the servers connected to the Internet.
To summarize, the flaw, called “Heartbleed,” allows an attacker to use messages called “heartbeats” to trick a server into passing along sensitive information from its memory, which could include account passwords or the server’s private encryption keys. When hackers get access to that information, really bad things can happen.
So what can you do in response to the Heartbleed vulnerability? In all honesty, not too much. Assume the worst-case scenario, that an attacker has compromised your online passwords, so consider updating your passwords for affected websites to one that’s longer and more difficult to crack. You should also activate multi-factor authentication for any service where it is supported.] Researchers have discovered a serious flaw known as Heartbleed that affects the security software that runs on about two-thirds of the servers on the internet and could expose user data, including passwords. Here’s what you need to know about it
Tiburon CEO Summit extrudes big news: Betterment Institutional is born from RIABiz.com
[Next is an update from the online investment advice category, as this week Betterment revealed plans to introduce an institutional version of its technology to financial advisors.
In a fascinating report, RIABiz detailed how plans for Betterment Institutional were made public this week at the Tiburon CEO Summit in New York, as Betterment CEO Jon Stein and new Betterment partner and investor Steve Lockshin, known for founding Fortigent and Convergent Wealth Advisors, were both in attendance.
The soon-to-be-released offering from Betterment takes direct aim at existing turnkey asset management platforms, or TAMPs, which include well-known names like SEI, Envestnet, Adhesion, and even Fortigent itself, with an ultra-low cost offering of around 35 basis points all in.
Cut-throat pricing isn’t the only attraction of Betterment Institutional, as both advisors and clients will likely benefit from access to Betterment’s slick online dashboards and mobile app support for Android and iPhone.
So if you’ve considered outsourcing your investment management and reporting to a TAMP, Betterment Institutional will be a solution that deserves your close attention over the coming months.] Steve Lockshin lays out his plans for TAMP-like venture and how Michael Kitces, a public critic of the Betterment CEO, very much fits in
Redtail and Riskalyze Launch Next-Generation Integration Partnership from Riskalyze.com
[And finally, rounding out this week’s update is news of a new integration between Redtail Technology and Riskalyze. Redtail, known for its CRM, email, and imaging solutions now synchronizes client assets with Riskalyze, a client risk tolerance assessment tool and my pick for best client-facing technology of 2013, on a nightly basis.
In the other direction, Riskalyze updates client risk scores based on the synchronized account information and pushes them along with the client Risk Numbers over to the client’s profile in Redtail CRM. This is a time-saving upgrade as users of both solutions will no longer have to manually switch back and forth to keep assets or Risk Numbers up to date.] Redtail, the industry leader in advisor CRM, email and imaging, and Riskalyze, the company that invented the Risk Number, today announced a next-generation integration partnership that delivers incredible tools for advisors to grow their practices.
And here are stories that didn’t make this week’s broadcast:
The Advisor’s Technology Swiss Army Knife from Morningstar Advisor
One advisor technology startup combines a suite of disparate business-development tools into one effective solution.







 In response, Dropbox said
In response, Dropbox said  After participating virtually (e.g. online) in what was likely the busiest shopping weekend of the year last week, I logged in to reconcile one of my credit card accounts. Lo and behold, they added a new security feature to authenticate my account when I used a second computer to log in.
After participating virtually (e.g. online) in what was likely the busiest shopping weekend of the year last week, I logged in to reconcile one of my credit card accounts. Lo and behold, they added a new security feature to authenticate my account when I used a second computer to log in.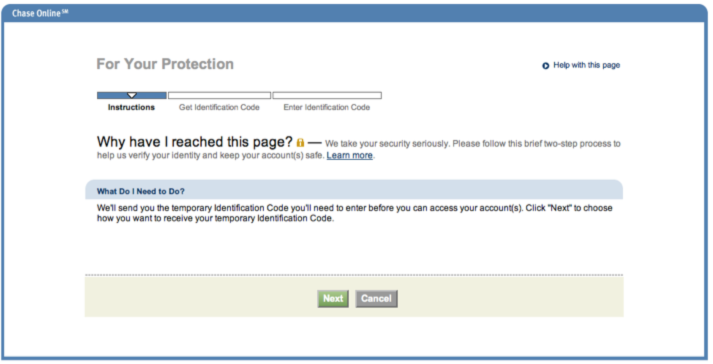 After clicking Next, I was given the option of receiving my code using several contact methods associated with my account profile. Options included voice or text messages to one of my phone numbers or receiving a code via an email account previously registered to my account.
After clicking Next, I was given the option of receiving my code using several contact methods associated with my account profile. Options included voice or text messages to one of my phone numbers or receiving a code via an email account previously registered to my account.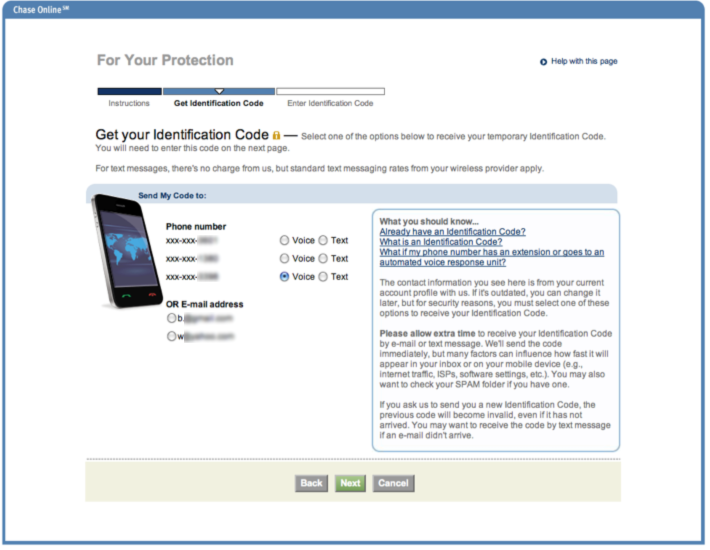 Just as in my
Just as in my 


