“Spoofing” is on the rise and RIAs are becoming targets of clients that are not who they appear to be.

What seemed like ordinary correspondence from a client quickly became a compliance nightmare for one Dallas-based wealth management firm.
I recently spoke with an executive from the Dallas-based firm who asked to remain anonymous due to ongoing investigations about the incident. This person described how the firm received a wire request from a client via email, so the firm replied by sending the appropriate form for a client signature. A few hours later the form was returned and the signature was compared with another from a prior wire request already on file. Everything looked to be in good order.
But unfortunately for all parties involved, the wire request was not from the actual client, but from someone who had broken in to the client’s email account.
Client Spoofing
It turns out this scenario is not unique, as over a half-dozen cases involving Dallas/Ft. Worth-based RIAs have been reported since the beginning of the year.
In the latest scheme to defraud individuals, hackers are using “spoofing” techniques to impersonate others who have relationships with professional financial advisers. Spoofing is commonly accomplished by obtaining a client’s email account password through keylogging software or by substituting indistinguishable characters in valid email address (e.g. lower-case “l” and a capital “I”). In either case, the hacker attempts to exploit the existing trusted relationship with the adviser who has no reason to be suspicious of a request to transfer funds.
In addition to client impersonation through email, some hackers are going so far as to activate call forwarding on a client’s personal cell phone account, meaning that confirming a client’s wire instructions via phone may not always guarantee the person on the other end is who they say they are. The boldest of hackers are calling in directly to advisory firms, spoofing Caller ID, and verbally requesting wire transfers.
If a firm’s back office staff has little or no contact with certain clients, employees have little opportunity to properly validate the identity of the individual calling in.
Combating Spoofing
Since you can no longer trust the authenticity of all correspondence received from clients, either by email or phone, what can you do to protect yourself and your clients from spoofing activity?
There’s no clear consensus on best practices to combat client spoofing. Remember that verifying instructions by placing a phone call can be insufficient if the hacker is able to activate call forwarding on a victim’s phone.
One recommendation is to follow the authentication practices of large banks and credit card companies. When you call in as a customer, you’re asked for a secret word or phrase in addition to your account information to proceed with any assistance. While one’s mother’s maiden name is often the typical security word, I would advise against using it for your authentication process.
You may want to update your policies and procedures to ask for clients’ secret phrase before processing fund transfers of any kind. Keep this secret phrase secure and confidential, likely included in your password-protected CRM software next to your client’s contact record.
Also, in the age of camera-equipped mobile devices, a video chat to confirm wire instructions is a better way to verify a client’s identity versus a standard phone call. Still, the employee at the advisory firm must know what the client looks like before contacting him/her to verify instructions!
If You’re Targeted
If you believe your firm is the target of client spoofing, one good place to report the incident is the Internet Crime Complaint Center, or IC3 (http://www.ic3.gov/). IC3 is a partnership between the Federal Bureau of Investigation (FBI) and the National White Collar Crime Center (NW3C) and aggregates incident reports to allocate investigative resources accordingly. Often, the FBI or the Secret Service will get involved in cases involving spoofing of investment adviser clients.
Educate Clients
Finally, one weak link in most spoofing scenarios is a client’s password credentials to web-based email accounts. A value-add service you can provide to clients is education on how to best protect login and password credentials. Sage advice includes never entering credentials using an unknown computer, such as a public computer in a hotel business center.
Also, an increasing number of web-based email providers allow users to enable multi-factor authentication to the login process. I addressed multi factor authentication in this Morningstar Advisor column, which requires users to authenticate their login activity through a second device, typically via SMS text messages. Even many credit card companies are employing this additional verification process to their systems.
So don’t fall victim to the next spoofing attack your firm encounters. It’s not a question whether if an attack will occur, but rather when.
More resources on spoofing:


 In response, Dropbox said
In response, Dropbox said 

 After participating virtually (e.g. online) in what was likely the busiest shopping weekend of the year last week, I logged in to reconcile one of my credit card accounts. Lo and behold, they added a new security feature to authenticate my account when I used a second computer to log in.
After participating virtually (e.g. online) in what was likely the busiest shopping weekend of the year last week, I logged in to reconcile one of my credit card accounts. Lo and behold, they added a new security feature to authenticate my account when I used a second computer to log in.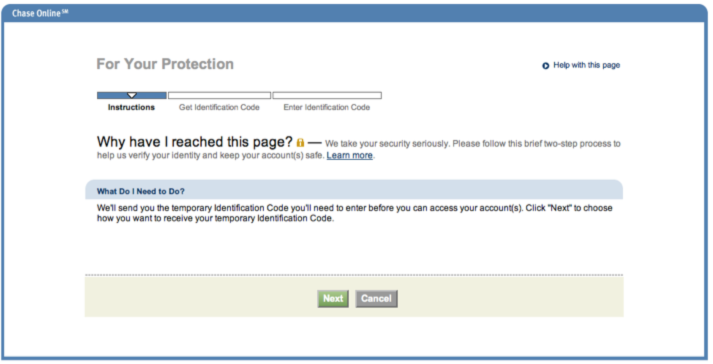 After clicking Next, I was given the option of receiving my code using several contact methods associated with my account profile. Options included voice or text messages to one of my phone numbers or receiving a code via an email account previously registered to my account.
After clicking Next, I was given the option of receiving my code using several contact methods associated with my account profile. Options included voice or text messages to one of my phone numbers or receiving a code via an email account previously registered to my account.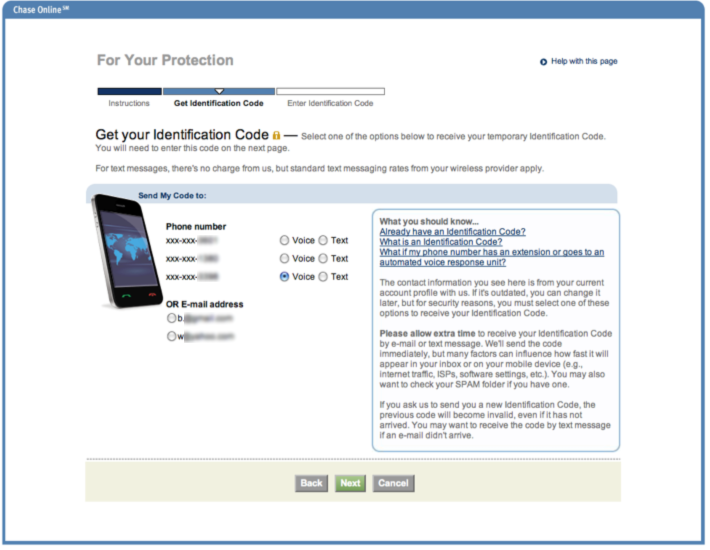 Just as in my
Just as in my 
 This article was originally posted on April 29, 2010 to
This article was originally posted on April 29, 2010 to 


